Data communication discusses the transfer of information from one device to another. The protocol defines the rules for communication so that the sender and receiver can coordinate their activities. At the physical layer, information is converted into signals that can be transmitted over wired media (copper or fiber optic cable) or wireless media (radio or infrared transmission). High-level protocols define the encapsulation of transport information, flow control, and recovery techniques that are lost or corrupted in transmission.
letter of agreementThe communication protocol can be likened to the diplomatic agreement used in the diplomatic embassy. Diplomats at all levels are responsible for handling different types of agreements. They contacted diplomats at the same level as other embassies. Similarly, communication protocols have a layered architecture. When two systems exchange data, the protocols in each layer communicate with each other to handle various aspects of the communication. Figure D-2 is a short form.
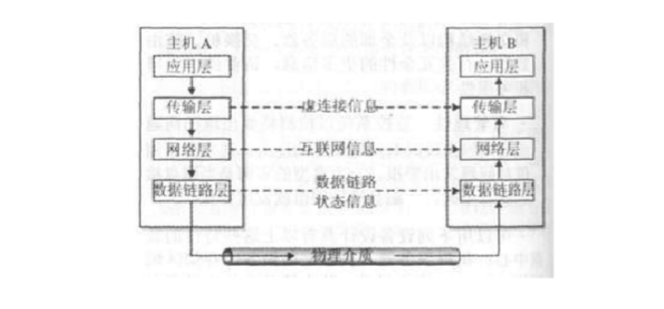
Figure D-2 Schematic diagram of hierarchical network structure
A long time ago, ISO (International Organization for Standardization) developed the OSI (Open Systems Interconnection) model in 1979. The model adopts a hierarchical structure, and the network protocol is divided into seven levels, which are physical layer, data link layer, network layer, transport layer, session layer, presentation layer and application layer from bottom to top. The function of each layer and its interface with the adjacent layer are specified in the model. Networks designed and built according to the Open System OSI Interconnect Reference Model are open and interconnectable to ensure that the world's networks are connected. Although the OSI model has never been a popular standard, it is still used to describe protocol layering.
What is a data communication protocol?Data communication protocols are also known as data communication control protocols. It is a series of conventions prescribed to ensure effective and reliable communication between the two parties in the data communication network. These conventions include the format, order and rate of data, confirmation or rejection of data transmission, error detection, retransmission control and interrogation. There are two types of data communication protocols: one is called basic communication control protocol, which is used for data transmission based on characters, such as BSC protocol (binary synchronous synchronous communication protocol); the other is called advanced key control protocol. Used for bit-based data transmission, such as HDLC (Advanced Data Link Control Protocol) and SDLC (Synchronous Data Key Control Protocol).
Characteristics of data communication protocolsData communication protocols have two distinct features:
First, they all adopt a hierarchical structure. A network architecture is actually a collection of communication functional layers and protocols. In an open system, each end system must implement a seven-layer protocol in the open system interconnection reference model, and the relay system executes its lower three-layer protocol.
Second, data communication protocols are all in the form of standards. The standards mentioned here include international standards and standards of companies from various countries. The international standards for data communication protocols mainly include relevant CCITT recommendations and ISO standards. The CCITT proposal is based on the data communication network. The ISO standard is based on the network terminal system, and the corresponding protocol standards of the two are compatible with each other. CCITT's main recommendations for data communication protocols are V-series recommendations, X-series recommendations, T-series recommendations, and I-series recommendations. The V-series recommendations specify the data transmission protocol in the telephone network (X-series recommendations systematically specify data communication network services and service functions, network architecture, network interconnection, mobile data communication, network numbering scheme, data transmission quality, Protocols such as network management and security architecture, and application protocols such as message processing systems and directory queries; the T-series recommendations specify data communication protocols for data communication in the Integrated Services Digital (ISDN).
Engineering technology of data communication protocolThe main technology of the practical application of the agreement. It mainly includes protocol formal description technology, protocol verification technology, protocol analysis technology and protocol conformance testing technology.
1. Protocol formal description technology
Protocol formal description technology is a technique for explaining a given protocol by using a language with formal grammar or semantics (including state diagrams, etc.), and is an effective means for implementing the basis of the protocol. Ambiguity and a representation technique that can be explained uniquely. CCITT and ISO have successively developed three formal description techniques: SDL (Description and Description Language), ESTELLE (Extended State Transfer Language) and LOTOSC Timing Description Language.
2. Protocol verification technology
The protocol verification technique proves whether the described object satisfies the protocol specification technique. The main methods are:
The 1 state transition method utilizes a state transition diagram to represent the various properties of the protocol and the authentication protocol. This method is easy to detect deadlock and detect the possibility of a special state, and can also be automatically implemented by a computer. The disadvantage is that when the protocol size is increased and complicated, the number of states increases, and computer processing is more difficult. This method is mostly used for event exchange between communication processes that have been modeled.
2 The programming language method is based on a high-level programming language such as PASCAL, and adds a verification method suitable for a language specification formed by a fixed command set representing a protocol. This method can be used to verify the processing procedures for parameters such as serial numbers and timing values ​​that are difficult to verify with the state transition method.
3 The sequential logic method adds the specification description verification method of the time operator based on the logical operators (logical sum, logical multiplication, consent, negation, etc.). This method has strong verification capability for protocol survivability and security, but when the protocol scale is large, the comprehensibility of the description content is reduced, and verification becomes difficult.
The 4 algebraic method uses the description of the operation, parameters (define domain, value domain) and axioms to specify the verification method of the protocol specification. The advantage of this approach is that the protocol specification is given as an axiom, and the validation and protocol specification descriptions can be discussed in the same framework. The disadvantage is that when the protocol is large, the comprehensibility is reduced and maintenance becomes difficult.
3. Protocol Analysis Technology
The protocol analysis technology is a technology for judging and correcting the execution status of the protocol in the process of protocol development, testing, and maintenance, thereby determining the correctness of the protocol execution. Protocol analysis is achieved by using a protocol analyzer in both monitoring and simulation. The monitoring method is that the protocol analyzer displays and stores the data signals received from the line for the operator to judge and analyze. The analog mode is to replace the host computer or terminal with a protocol analyzer, and check and analyze the correctness of the protocol executed by the device under test under the pre-programmed program control.
Protocol conformance testing techniques are techniques for testing the degree of consistency between protocol implementations and protocol standards in data communication systems. Its purpose is to improve interoperability between data communication devices.
Fume Ultra Vape,Fume Ultra Disposable Vape,Fume Ultra Disposable 2500 Puffs,Fume Ultra 2500Puffs Vape
Nanning Nuoxin Technology Co., LTD , https://www.nx-vapes.com