Firewalls often appear on the network as two icons shown below. The icon on the left is very image, really like a wall. The icon on the right is visualized from the filtering mechanism of the firewall. There is a diode icon in the icon. The diode we know, it has one-way conductivity, so it also shows that the firewall has unidirectionality. This appears to be somewhat in conflict with the current firewall filtering mechanism, but it fully embodies the initial design of the firewall, but also to a considerable degree reflects the current firewall filtering mechanism. Because the original design idea of ​​fire prevention was always trusting the internal network, but it was always not trusted by the external network. Therefore, the original firewall filtered only external incoming traffic and did not restrict the communication sent by internal network users. . Of course, current firewalls have changed in the filtering mechanism. Not only do the communication connections from external networks need to be filtered, but also some of the connection requests and data packets sent by internal network users need to be filtered. However, the firewall still only communicates to security policies. Passed, it can also be said to have "universal guidance".
The original meaning of the firewall refers to the ancient construction and use of wooden houses. In order to prevent the occurrence and spread of fire, people build a solid stone around the house as a barrier. Such protective structures are called “firewallsâ€. In fact, it works with the firewall is the "door." If there is no door, how do people in each room communicate? How do people in these rooms enter? When a fire broke out, how did these people flee the scene? This door is equivalent to the "security policy" of the firewall we are talking about here, so the firewall we are talking about here is not actually a solid wall, but a wall with some small holes. These holes are used to allow those communications that are allowed to be carried out, and a filtering mechanism is installed in these holes, which is the "unidirectional" described above.
What we often call a network firewall is a metaphor for firewalls that were really used for fire protection in ancient times. It refers to a defense system that is isolated between the local network and the outside world. Fire protection can isolate the intranet (LAN) network between the enterprise and the Internet or other external networks and limit network access to protect the internal network. A typical firewall has the following three basic characteristics:
(1) All network data flow between the internal network and the external network must pass through the firewall. This is the characteristic of the network location of the firewall, and it is also a prerequisite. Because only when the firewall is the only channel for communication between internal and external networks, can fully and effectively protect the corporate network network from being infringed.
According to the "Information Security Technology Framework" developed by the US National Security Agency, the firewall is applicable to the border of the user's network system and belongs to the security protection device at the user's network boundary. The so-called network boundary refers to two network connections using different security policies, such as the connection between the user network and the Internet, the network connection with other business contacts, and the connection between different departments of the user's internal network. The purpose of the firewall is to establish a security control point between network connections. By permitting, refusing, or redirecting traffic passing through the firewall, the firewall can implement auditing and control of services and access to and from the internal network.
The typical firewall system network structure is shown in the figure below. As can be seen from the figure, one end of the firewall is connected to the local area network within the enterprise and the other end is connected to the Internet. All communications between internal and external networks go through the firewall.
(2) Only the flow of data that complies with the security policy can pass through the firewall The basic function of the firewall is to ensure the validity of network traffic. In this context, the network traffic is quickly forwarded from one link to another. Starting from the earliest firewall model, the original firewall is a "double-homed host", which has two network interfaces and has two network layer addresses. The firewall receives traffic on the network through the corresponding network interface, uploads it in the order of seven layers of the OSI protocol stack, performs access rules and security audits at the appropriate protocol layer, and then passes the packet that meets the pass criteria from the corresponding network interface. Send out, and block those messages that do not meet the pass criteria. Therefore, from this perspective, a firewall is a multi-port (network interface >=2) forwarding device similar to a bridging or router. It is connected across multiple separate physical network segments and forwards packets. The review of the message was completed during the process.
(C) The firewall itself should have a very strong anti-attack immunity This is a precondition for the firewall to be able to play the role of internal network security protection. The firewall is at the edge of the network. Like a border guard, it faces hacker attacks every moment. This requires the firewall to have a very strong ability to resist intruders. The reason why it has such a strong firewall operating system itself is the key, only the operating system with its own complete trust relationship can talk about the security of the system. The second is that the firewall itself has very low service capabilities. In addition to a dedicated firewall embedded system, there are no other applications running on the firewall. Of course, these security can only be said to be relative.
At present, domestic firewalls are almost occupied by half of the foreign brands. The advantages of foreign brands are mainly higher in technology and popularity than domestic products. The domestic firewall manufacturers have more thorough understanding of domestic users, and they have more advantages in terms of price. Among the firewall products, the mainstream foreign vendors are Cisco, CheckPoint, NetScreen, etc. The domestic mainstream vendors are Neusoft, TOPSEC, Lenovo, Founder, etc. They all provide different levels of firewall products.
Rechargeable Vacuum Cleaner is also a Handheld Vacuum Cleaner. Some rechargeable Vacuum Cleaner has charger base with multifunction,so we can store easier. Although it is basic configuration,it has complete accessories. So you can use in any places. Its basic configuration's battery is NI-CD(1200MAH),but if you want to change,it is allowed. You can change to NI-HI battery or battery pack. If the battery is Replaced,the unit price will change,too. So please consider clearly. Now I will show you some pictures about rechargeable vacuum cleaner.
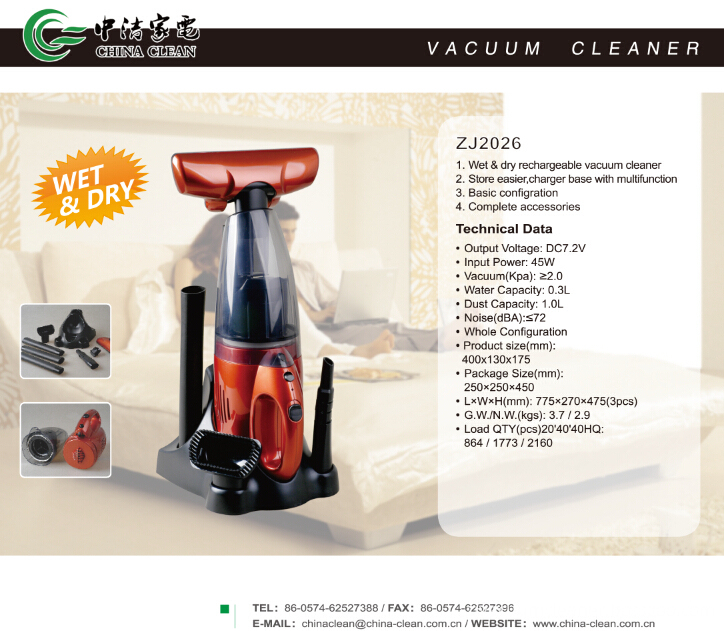



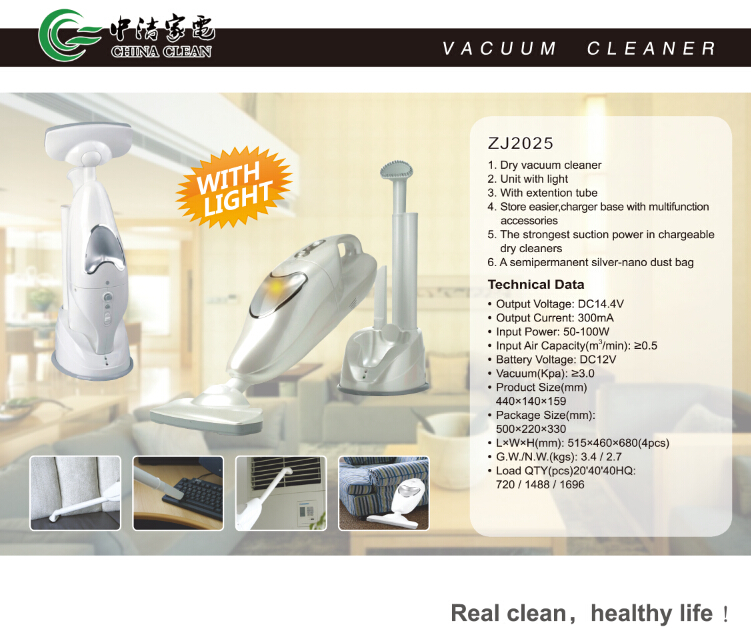
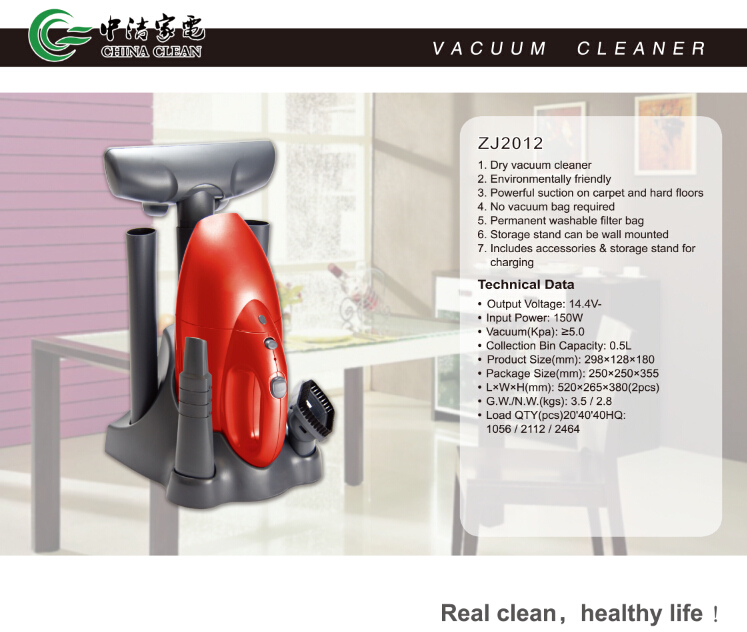

Rechargeable Vacuum Cleaner
Rechargeable Vacuum Cleaner, Rechargeable Car Vacuum Cleaner, Cordless Rechargeable Vacuum Cleaner, Rechargeable Upright Vacuum Cleaner
Ningbo ChinaClean Household Appliances Manufacture Co., Ltd. , http://www.chinaclean-elec.com